Cyber threats come in many forms and can severely impact business operations, brand reputation, financial standing and even lead to a lawsuit. Organizations must prepare to respond and manage cyber events at different organizational levels to limit their damage and accelerate recovery.
Most businesses focus on incident management or crisis management to react to cyber attacks. Both provide different aspects of response. And, both have a unique set of objectives.
Learn the key differences between incident management and crisis management to decide which response plan is best for your company.
Cyber Events Types
Cyber events must be appropriately classified to activate stakeholders at the necessary organizational levels to ensure an adequate response. An incident is an adverse security event that negatively impacts or poses an imminent threat to the confidentiality, integrity or availability of data, including technologies that store and process that data. This definition also includes explicit or implied security policy violations.
Cyber incidents are generally classified by magnitude: minor incident, major incident and crisis.
Minor Incident
Incidents that insignificantly affect organizations are defined as minor incidents. Enterprises typically qualify incidents as minor when they do not cause a notable operational or informational impact on their business. These usually can be handled as part of day-to-day operations. For example, commodity malware that infects an end-user workstation typically qualifies as a minor incident.
Major Incident
A cyber event becomes a major incident when it causes a functional or informational impact on the organization. This requires an urgent response beyond day-to-day operations.
An informational impact occurs when a cyberattack negatively affects the confidentiality or integrity of data. In contrast, a functional impact occurs when a cyberattack impairs the functionality of a computer system, causing a negative effect on business operations.
Major incidents require the activation of a cybersecurity incident response team (CSIRT) or another cross-functional team responsible for coordinating and supporting the incident response effort. Organizations should designate an incident manager to coordinate the incident response effort between stakeholders and manage the different facets of major incident response.
For example, a threat actor exploits a vulnerability in a web application which processes payment card data. This event becomes a major incident because it threatens the confidentiality of the data and requires an immediate and coordinated response.
Crisis
A crisis occurs when specific cyber events significantly affect business operations, brand reputation, financial standing or threaten the existence of an enterprise. For example, ransomware encrypts systems that support a business’ core functions. The affected enterprise has no alternative arrangements to continue business operations so the incident becomes a crisis.
A crisis management team is critical in determining the wider business impact and setting a strategy and business priorities. A ransomware containment strategy may require temporary or long-term disablement of critical infrastructure. This may result in lost revenue, customer trust or business service availability. The decision to execute with a containment strategy is a business decision and should be made by the crisis management team.
Incident Management
An incident response plan (IRP) is action-oriented and focuses on tactical response. Tactical response refers to technical activities required to address the event, but may also involve various corporate functions. Organizations create incident management plans to establish a repeatable and consistent process to handle minor and major incidents from a tactical perspective.
For example, a threat actor gains unauthorized access to a system that handles highly-sensitive data. The company’s legal counsel may invoke appropriate protocols to conduct an internal investigation, protect the incident communication and reduce the risk of legal exposure.
Different types of incidents require different leadership structures to ensure effective and efficient allocation of organizational resources. Organizations manage minor incidents as part of day-to-day security operations. Because of their limited impact, there is no need to activate a CSIRT or assign a dedicated incident manager. However, a security manager or appropriate stakeholder may need to be activated in a particular CSIRT function. This can include cyber events resulting from employee misconduct.
It is important to note that inadequately addressed minor incidents can swiftly progress into a major incident or even a crisis.
In contrast, a major incident requires the activation of a CSIRT and a dedicated incident manager. The incident manager coordinates various response activities across security, corporate, technology and third-party functions. In some cases, organizations may need to assign an incident commander, also known as an incident officer, to provide strategic direction and set response priorities. The incident commander also also provide regular updates to senior managers.
Crisis Management
Crisis management is a natural extension of major incident management. Both run in parallel during a significant incident. However, a crisis management plan’s primary goal is to ensure operational resiliency. It dictates how to activate core leadership across an organization.
A data breach or ransomware incident may have a significant impact on an organization’s tangible assets, such as the availability of their computing environment. But, the breach can also affect intangibles, such as brand reputation and trustworthiness. A crisis management plan is focused on communication and decision making around the associated risks.
During a crisis event, an enterprise should convene a crisis management committee and activate their business continuity plan. Executive management forms the crisis committee to handle the crisis from a strategic perspective and set business priorities for tactical response. The areas of responsibility of the crisis committee include public relations, shareholder management, updates to regulators and brand reputation management.
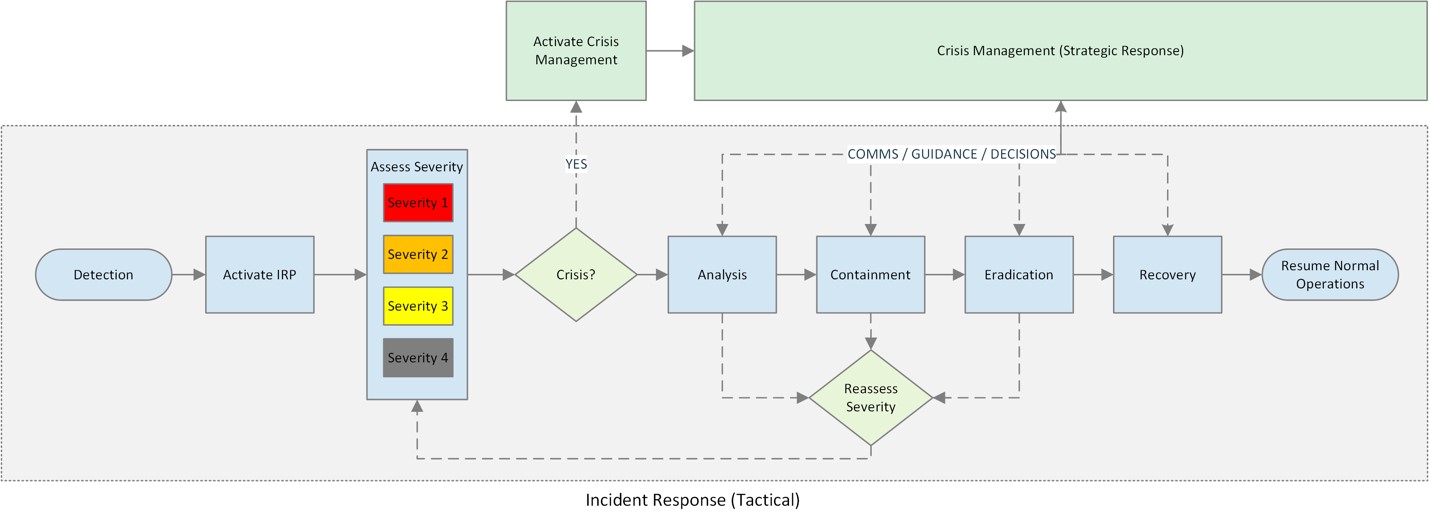
Figure 1: This chart depicts the relationship between incident response and crisis management.
Plan Communication
Crisis management is a natural extension of major incident management. Crisis management and incident management run in parallel during a significant incident. There is downstream and upstream communication between both.
Communication is a significant element of both an incident response and crisis management plan. Incident response communication focuses on coordinating the response effort among stakeholders and ensuring they have the necessary information to fulfill their responsibilities.
Crisis communication focuses on brand reputation management and communicating with vital stakeholders, such as the public, shareholders, business partners or regulators.
Incident management and crisis management are not mutually exclusive. Enterprises must develop both plans to prepare for and handle cyber events with varying degrees of magnitude. Both response plans are different but use related documents that allow organizations to address cyber events at various organizational levels.
X-Force Incident Response and Intelligence Services helps clients develop actionable incident response and cyber-focused crisis management plans to prepare for significant cyber events effectively and accelerate response activities.
You can find out more about building incident response capabilities in the book “Cyber Breach Response That Actually Works: Organizational Approach to Managing Residual Risk.” The book is available for purchase on Amazon and other major retail stores.
"between" - Google News
July 16, 2020 at 06:07PM
https://ift.tt/3jbhK9h
Deciphering Between Incident Management and Crisis Management - Security Intelligence
"between" - Google News
https://ift.tt/2WkNqP8
https://ift.tt/2WkjZfX
Bagikan Berita Ini















0 Response to "Deciphering Between Incident Management and Crisis Management - Security Intelligence"
Post a Comment