Cybersecurity reports often talk about threat actors and their malware/hacking operations as self-standing events, but, in reality, the cybercrime ecosystem is much smaller and far more interconnected than the layperson might realize.
Cybercrime groups often have complex supply chains, like real software companies, and they regularly develop relationships within the rest of the e-crime ecosystem to acquire access to essential technology that enables their operations or maximizes their profits.
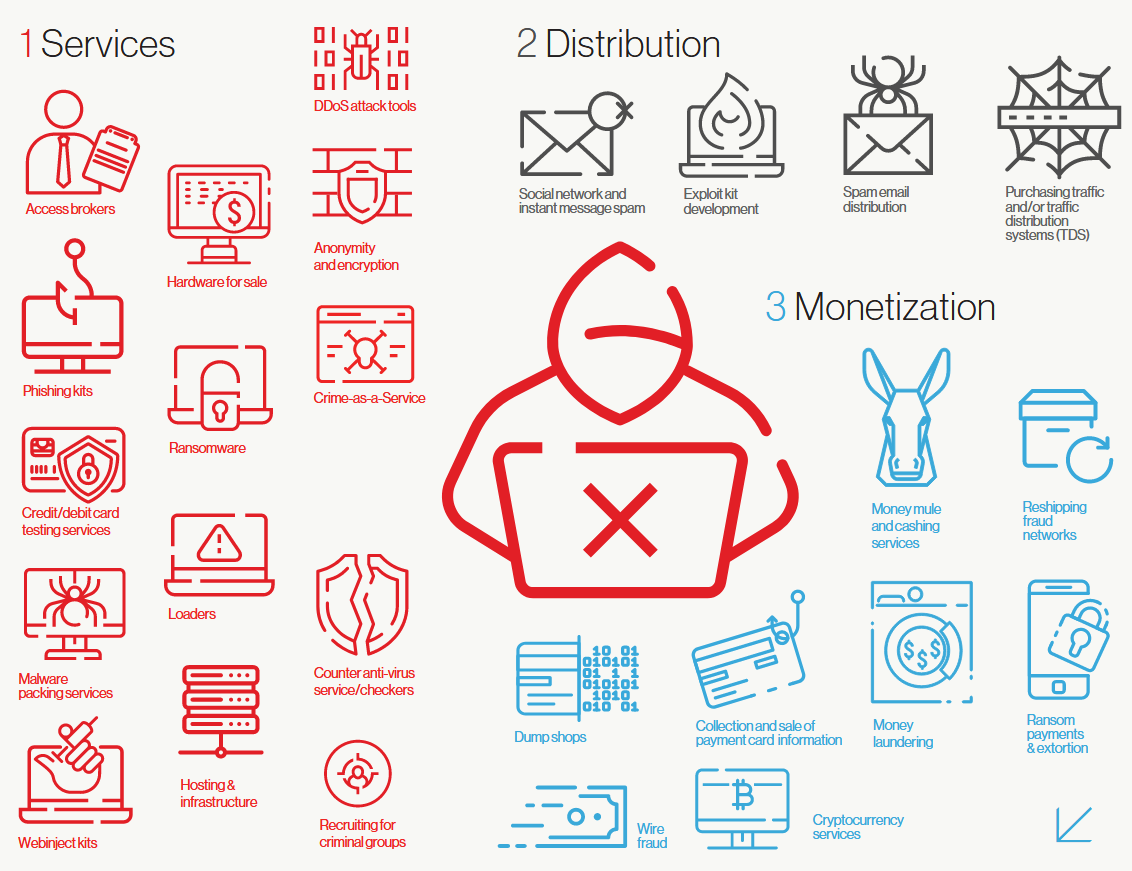
According to cybersecurity firm CrowdStrike, these third-party technologies can be classified into three categories: services, distribution, and monetization.
Breaking down each, the services category usually includes:
- Access brokers - threat actors who breach corporate networks and sell access into a company's internal network to other gangs.
- DDoS attack tools - also known as DDoS booters or DDoS-for-hire, these groups provide access to web-based panels from where anyone can launch a DDoS attack against a target.
- Anonymity and encryption - threat actors who sell access to private proxy and VPN networks, so hackers can disguise their location and origin of their attacks.
- Phishing kits - threat actors who create and maintain phishing kits, web-based tools used to automate phishing attacks, and the collection of phished credentials.
- Hardware for sale - threat actors who sell custom-made hardware, such as ATM skimmers, network sniffing devices, and more.
- Ransomware - also known as Ransomware-as-a-Service, or RaaS, these groups sell access to ransomware strains or a web-based panel where other gangs can build their own custom ransomware.
- Crime-as-a-Service - similar to RaaS, but these groups provide access to banking trojans or other forms of malware.
- Loaders - also known as "bot installs," these are threat actors who already infected computers, smartphones, and servers with their own malware and offer to "load/install" another group's malware on the same system, so the other group can monetize it through ransomware, banking trojans, info-stealers, etc.
- Counter antivirus service/checkers - these are private web portals where malware devs can upload their samples and have them tested against the engines of modern antivirus systems without the fear of the malware's detection being shared with the AV maker.
- Malware packing services - these are web-based or desktop-based tools that malware developers use to scramble their malware strain's code and make it harder to detect by antivirus software.
- Credit/debit card testing services - these are tools that hackers use to test if the payment card numbers they acquired are in a valid format and if the card is (still) valid.
- Webinject kits - these are specialized tools, usually used together with banking trojans, to allow a banking trojan gang to insert malicious code inside a victim's browser while they visit an e-banking (or any other) site.
- Hosting & infrastructure - also known as bulletproof hosting providers, their name is self-evident as they provide private web hosting infrastructure specifically tailored for criminal gangs.
- Recruiting for criminal purposes - these are specialized groups that recruit, bribe, or trick normal citizens into participating in a cybercrime operation (e.g., someone who travels to the US in an attempt to bribe a Tesla employee to run a malicious tool inside the company's internal network).
On the other hand, distribution services include the likes of:
- Groups that run spam campaigns on social networks or instant messaging apps.
- Groups specialized in email spam distribution.
- Groups who develop and sell exploit kits.
- Groups who purchase traffic from hacked sites and distribute it to malicious web pages that usually host exploit kits, tech support scams, financial scams, phishing kits, and others.
As for monetization services, Crowdstrike says this category usually includes:
- Money mule services - groups who offer to physically show up and pick up money from hacked ATMs, receive money in their bank accounts, and then redirected to the hackers, their preferred money laundering or reshipping fraud service.
- Money laundering - groups who often operate networks of shell companies through which they move funds from hacked bank accounts, ATM cash-outs, or cryptocurrency heists. Some money laundering services also operate on the dark web as Bitcoin mixing services.
- Reshipping fraud networks - groups that take stolen funds, purchase real products, ship the products to another country. The products, usually luxury goods like cars, electronics, or jewelry, are then resold and converted into clean fiat currency that's transferred to the hackers who contracted their services.
- Dump shops - groups that sell data from hacked companies via specialized websites and social media channels.
- Ransom payments & extortion - groups specialized in extorting victims, and which can be contracted by other gangs in possession of stolen data.
- Collection and sale of payment card information - also known as carding shops, these are typically forums where cybercrime groups go to sell stolen payment card data.
- Cryptocurrency services - a form of money laundering, these services offer to "mix" stolen funds and help hackers lose the trail of stolen funds.
- Wire fraud - as the name says, groups that are specialized in performing wire fraud, such as BEC scams.
Tracking all the connections between groups and their suppliers and who works with who is almost impossible today due to the broad use of encrypted communication channels between parties.
However, in the realm of malware attacks, some signs of cooperation can be observed by the way the malware moves from attackers to infected hosts.
Although these connections can never be fully verified, it's also pretty obvious that when the Emotet malware is downloading the TrickBot malware that the two gangs are cooperating as part of a "loader" mechanism provided by the Emotet crew for the TrickBot gang.
In its 2021 Global Threat Report, released on Monday, security firm CrowdStrike has, for the first time, summarized some of the connections that currently exist on the cybercrime underground between various e-crime operators.
The company uses its own nomenclature for e-crime groups, so some group names might sound different from what we've seen before. However, CrowdStrike also provides an interactive index so anyone can learn more about each group and link it to the names used by other companies.
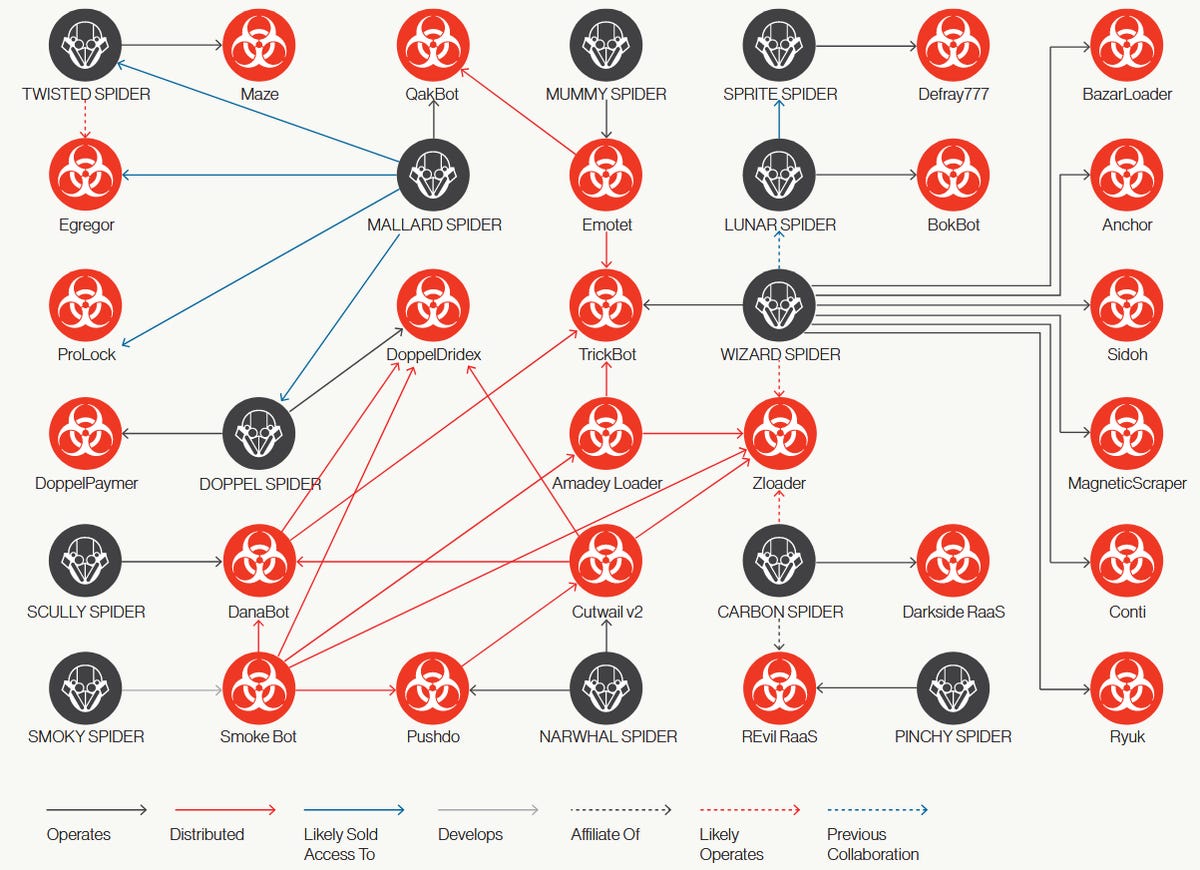
What the chart above shows is that enablers play just as important a role in cyber-intrusions as the groups executing the intrusion.
As Chainalisis pointed out in a separate report last month, law enforcement agencies are most likely to achieve better results in disrupting cybercrime operations when targeting these shared service suppliers, as they could end up disrupting the activities of multiple cybercrime groups at once.
Furthermore, there are also other benefits. For example, while top-tier cybercrime gangs often have top-notch operational security (OpSec) and don't reveal any details about their operations, targeting lower-tier enablers, who don't always protect their identities, could providing law enforcement agencies with data that could help them unmask and track down the bigger groups.
"between" - Google News
February 25, 2021 at 09:04PM
https://ift.tt/3dM3mnR
This chart shows the connections between cybercrime groups - ZDNet
"between" - Google News
https://ift.tt/2WkNqP8
https://ift.tt/2WkjZfX
Bagikan Berita Ini















0 Response to "This chart shows the connections between cybercrime groups - ZDNet"
Post a Comment